An effective and comprehensive cyber risk assessment program helps evaluate cyber threats, minimize vulnerabilities and impacts, and ensure controls are working. It gives you the knowledge to set priorities for improving your security posture and the confidence that you can identify and stop attacks, limiting their impact.
But not all cybersecurity assessment tools are created equal. If you depend on a risk assessment that is not comprehensive or not focused on the actual threats to your business, all you have is a false sense of security.
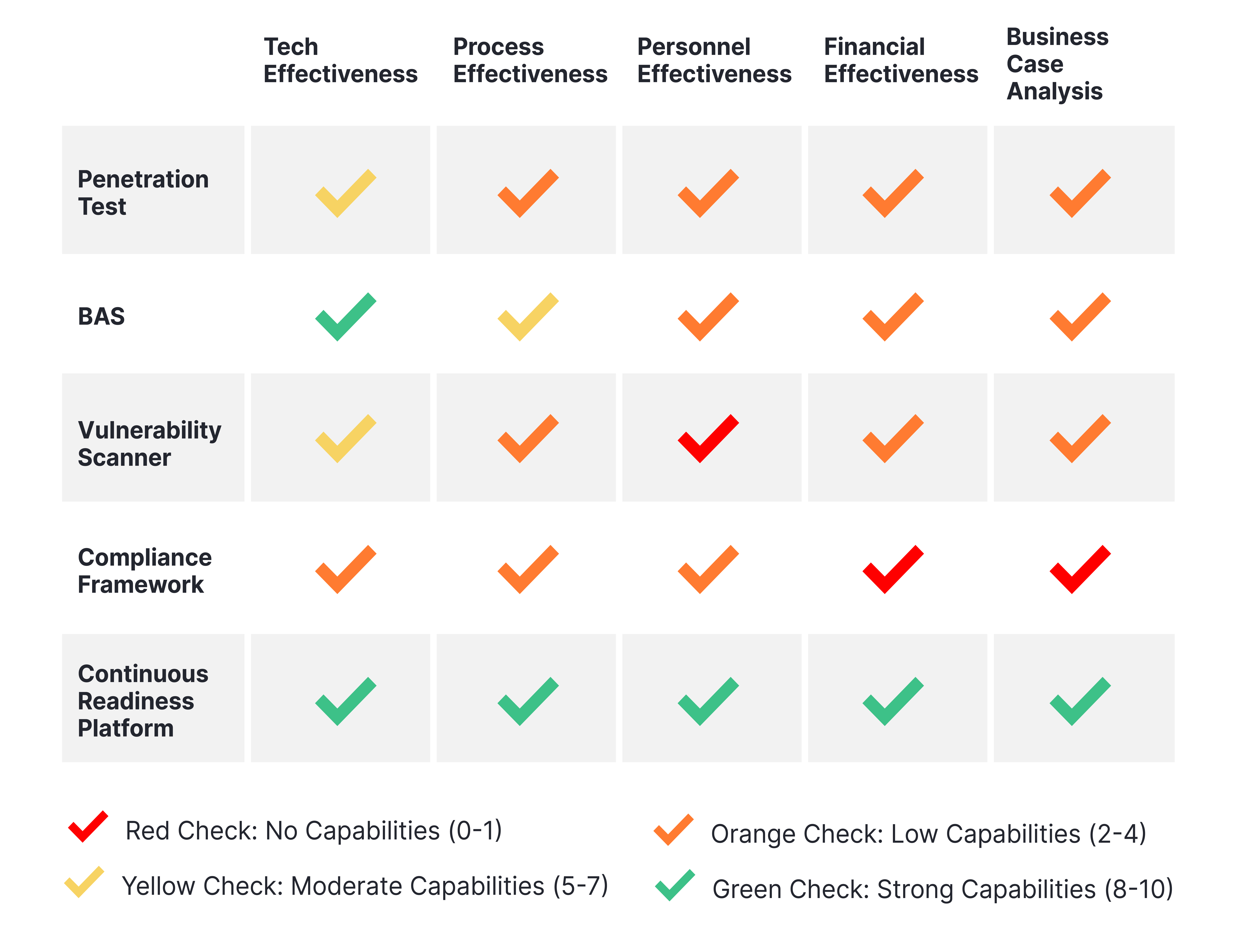
Current Cybersecurity Assessment Tools
How do you know if you are using the right cyber risk assessment tools? You need to consider the available tools, make an honest inventory of their strengths and weaknesses, and determine what gives you the visibility and actionable intelligence you need. Common tools used in cybersecurity risk assessments include:
- Penetration Tests: Manually executing malicious exploits on one or more computer systems or services, in order to evaluate their security.
- BAS (Breach and Attack Simulation): Executes simulated attacks against infrastructure to test cybersecurity prevention, detection, and response capabilities.
- Vulnerability Scanner: Automated testing and reporting of technical vulnerabilities in systems, including missing patches and some configuration errors.
- Compliance Framework: A set of guidelines and best practices that outline regulatory requirements and how to address them.
- Readiness Platform: A comprehensive platform that evaluates technology, processes, and people performance against real threats and provides the analytics to gauge effectiveness, risk exposure, and make informed business decisions.
Determining Effectiveness: Cybersecurity Assessment Tool Checklist
One or more of these tools may be the current foundation for your cyber risk assessment program. However, you must ask how effectively the tools you use are serving the purposes of a cyber risk assessment.
An effective cyber risk assessment covers five dimensions. Many tools provide some information about the effectiveness of security technologies, but that is only one of the things you need to learn from your assessment. Here are the other four:
- How well your processes are contributing to security, and details on how to improve processes.
- How effective your personnel are at finding and stopping attacks, and assignments to target training toward their gaps.
- What your level of financial exposure will be in the event of a breach.
- How your risk assessment findings can build the business case for security improvements.
This chart summarizes how well common cybersecurity assessment tools address the dimensions of risk:
The Advantages of Continuous Readiness
The mission of your security program is to keep your company and its data safe from real-world threats. Your cybersecurity assessments need to show you how well you are prepared to accomplish that mission. Incorporating a continuous readiness platform as the backbone of a readiness-based approach leads to better decisions in managing your cybersecurity program.
Readiness platforms have analytics capability built in, unlike other forms of cybersecurity assessments, which require separate procedures and capabilities for analytics. A readiness platform enables you to collect, view, and analyze empirical data about your company’s response to live-fire tests conducted with the platform.
With a continuous readiness platform, you gain insight into:
- Technology Effectiveness:
- Whether patches are addressing intended security vulnerabilities.
- Whether your controls actually work.
- Whether technical configurations are correct.
- Process Effectiveness:
- Whether your workflows actually work.
- What gaps exist in your defenses.
- Personnel Effectiveness:
- Whether personnel are able to identify threats in the SOC.
- Whether training is actually leading to increased proficiency in the SOC.
- Financial Exposure:
- Which systems and data are at an increased risk of compromise, based on current threat intelligence and threat performance test results.
- Business Case Analysis:
- What alternatives are recommended for identified gaps.
- Which security investments are providing the strongest returns.
With this information, you can tune technology, refine processes, and target analyst training based on identified gaps. The advantages also extend to making business decisions. A continuous readiness platform gives you the hard data you need to quantify business risk and track its change over time. It also helps you make business cases for security investments, and maximize the impact of a limited security budget.
Move Toward Readiness Today
We’ve seen it happen time and again. Unless you are continuously testing your readiness to face real threats, you are left guessing how effectively you can defend against attackers until they strike. By then, it is too late.
Now is the best time to make sure your cybersecurity risk assessment program can accomplish the mission of securing your business. A Continuous Readiness Platform can help you build a program that tests against real threats, assesses your progress, and gives you actionable empirical data with which to make confident security decisions. See for yourself how SightGain can help you focus on real cyber threats, increase your readiness, and make the most of your technologies, personnel, and budget.


