
Every organization has critical assets and functions that are required to perform its mission successfully. Fifty years ago, those assets were generally physical, and they were stored inside the walls of a building. A lock, an alarm, and a security guard were good enough to keep critical assets protected and it was easy to check if they were working. Fifty years ago, you never heard about a criminal gang breaking into a company to steal their HR records or customer loyalty files. Now, it’s a routine occurrence.
Today’s digital world expands the assets and functions that need to be protected. It also changes the techniques needed for protecting those assets and the methods used to make sure those protections are working.
How Do You Know When You’re “Secure”?
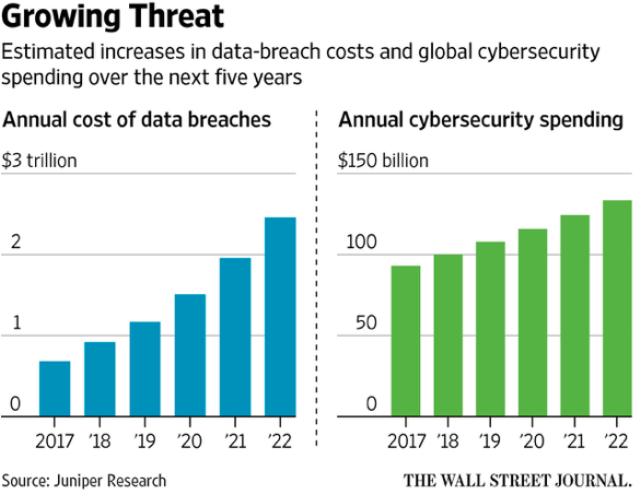
Given the growing importance of protecting digital assets and the challenge of doing so, it’s no wonder that cybersecurity spending has grown exponentially over the last few years and with no end in sight. Despite that increase in spending, only one thing is growing faster: the cost of cyber breaches. What’s the reason for this clear disconnection?
One answer is obvious: spending does not equal security. And yet, many leaders who are afraid to be seen as “doing nothing” use spending as a proxy for “doing something.” If a breach does happen, they can point to the zeros they’ve added to the end of their cybersecurity budget as a defense of how seriously they take the issue.
Another popular proxy for cybersecurity is the use of compliance frameworks like ISO 27001, NIST SP 800-82, and PCI DSS. In fact, the Cyber Experts blog lists the “Top 23 Cybersecurity Frameworks” that organizations should consider using. Unsurprisingly, despite a robust set of compliance frameworks, the result is the same as with spending: compliance does not equal security. Organizations that declare themselves “secure” after deploying new technology or passing the latest compliance audit may find they were already compromised in a way that audits don’t verify.
To summarize: organizations have collectively spent hundreds of billions on security and compliance, and the result has been trillions in losses from data breaches and cyberattacks. Regardless of how you look at it, no one can call this a success.
A Fundamental Question
There’s a better way to think about it. Instead of asking, “Are we secure?” organizations should be asking a fundamental question, “Are we ready to protect critical assets from the attacks they are likely to face?” This change in thinking can allow organizations to focus on the highest priority tasks, rather than everything. Because when you focus on everything, you focus on nothing. For example, only 1% of software vulnerabilities are ever exploited by attackers. However, most companies fail to test against that crucial 1%, largely because the current emphasis on vulnerabilities does not distinguish the other 99% of vulnerabilities that do not impact the current security posture.
Increasing the budget means buying another cybersecurity tool or hiring more people. Compliance means checking off a list of tools, software patches, and policies. Readiness means identifying what you need to protect, and then testing your security tools against actual cyberattacks to ensure they are working. Only by continuously testing and measuring their cybersecurity systems’ performance against real-world threats can leaders be confident that those systems are ready to protect against an attack.
What Is Cyber Readiness?
The concept of readiness is one that is well understood in military circles. The United States Department of Defense (DoD) defines readiness as “the ability of military forces to fight and meet the demands of assigned missions.” The military understands that readiness isn’t a simple binary state, and it defines three stages to readiness:
Building initial readiness
Increasing readiness
Sustaining readiness
The threats the military faces are constantly changing and evolving, so it must constantly assess the threat landscape and adapt and evolve its equipment, personnel, and training to be able to defend against those threats.This offers a key insight about readiness: it is threat-based, and it changes as threats change.
This concept of readiness is a useful framework for business leaders and security professionals when it comes to cybersecurity.
The ability of an organization to protect, detect, and respond to attacks against its critical digital assets and operational functions.
Like the military, businesses need to take a threat-based approach and constantly evaluate their readiness against the threats they face. They can also apply a similar three-stage process to cybersecurity readiness:
Determine current baseline level of readiness
Increase readiness by testing and improving their cybersecurity systems (people, process, and technology) performance against known real-world threats
Sustain readiness by continuing to test and tune their systems against the latest threats
As military leaders know, readiness requires consistent effort. Tactics developed for one type of terrain will be useless if units must fight in different terrain; equipment ages, breaks, and requires constant maintenance, repair, and replacement; weapon systems developed to confront one adversary may become obsolete if a new adversary emerges; and troops must constantly train to stay sharp. Without constant monitoring and reporting on the threat, readiness will not only drop, but almost as important, no one will know until it’s too late.
Similarly, security professionals and business leaders should be monitoring, reporting to their board, and working to improve their cyber readiness. This change in thinking is the first step for many businesses to start getting ahead of the threats.
How can you get an assessment of your cyber readiness? At SightGain, we’ve used our military experience and technical expertise to develop the world’s first cyber readiness platform, which helps organizations evaluate and improve their cyber readiness across all three critical components: people, process, and technology.
Cyber threats aren’t going away, and human adversaries are constantly hard at work developing the next exploit, whether you’re ready or not. Find out more at SightGain.com.

